VPN Subnet Translation
VPN subnet translation allows for a subnet that is allowed in the site-to-site VPN to be translated to a different, equally sized subnet. This option is ideal for deployments where the same subnet is used in multiple locations and each of those subnets need to have access to the site-to-site VPN.

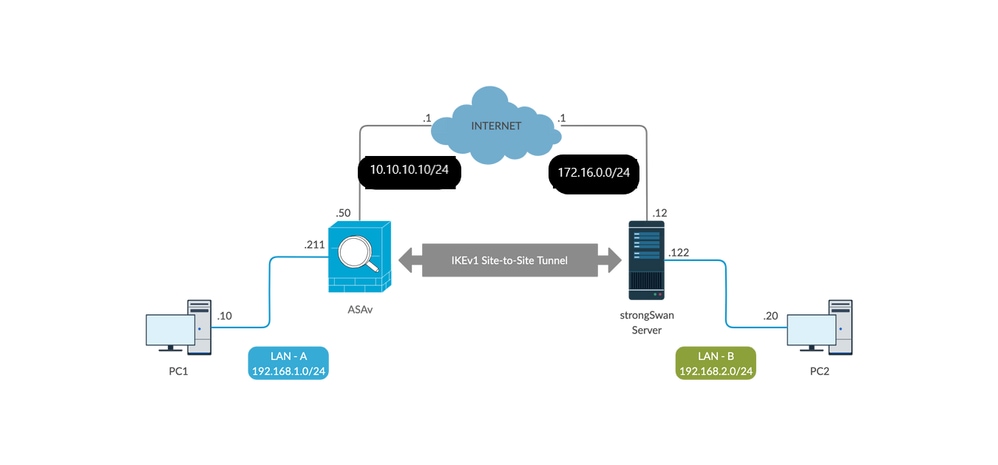
Site-to-Site IPSec VPN Tunnels are used to allow the secure transmission of data, voice and video between two sites (e.g offices or branches). The VPN tunnel is created over the Internet public network and encrypted using a number of advanced encryption algorithms to provide confidentiality of the data transmitted between the two sites. M@ttshaw thanks for your concern, let me tell you about the configuration settings. In site to site vpn wizard, i have mentioned the peer ip which is from remote site, in local network i have mentioned the specific machine ip not the whole network, and in remote network i have mentioned a object group, because the remote site ip's were different and from different networks, after that i have. Log in to the router web-based utility and choose VPN Client-to-Site. Click the Add button under IPSec Client-to-Site Tunnels section. Site-to-Site IPSec VPN Tunnels are used to allow the secure transmission of data, voice and video between two sites (e.g offices or branches). The VPN tunnel is created over the Internet public network and encrypted using a number of advanced encryption algorithms to provide confidentiality of the data transmitted between the two sites. Cisco VPN Clients are available for download from our Cisco Downloads section. The Cisco VPN also introduces the concept of ‘Split Tunneling'. Split tunneling is a feature that allows a remote VPN client access the company's LAN, but at the same time surf the Internet.
Configuration
To configure VPN subnet translation:
Vpn Client To Site Cisco Login
- Navigate to Security & SD-WAN >Configure > Site-to-site VPN.
- Set VPN subnet translation to Enabled. This will cause a new VPN subnet column to appear for the local networks.
- For the local subnet that must be translated, set VPN participation to VPN on with translation.
- In the VPN subnet column enter a subnet of the same size as the Local subnet.
- Select Save changes.
Operation
Please consider the following example:
- The 192.168.128.0/24 subnet exists in two locations
- The devices and users in this subnet at both locations need to access resources across a site-to-site VPN connection
- To avoid address and routing conflicts across the site-to-site VPN, 192.168.128.0/24 has been configured to be translated to 10.15.30.0/24
- A host on the corporate VLAN with an IP address of 192.168.128.44 is communicating with a web server across the site-to-site VPN with an address of 172.16.30.8
- The web server is also connected locally to another MX security appliance. This MX is a part of the site-to-site VPN.
Vpn Client To Site Cisco Server
When VPN subnet translation is configured, the MX will check the source IP address against a address translation table. When 192.168.128.44 attempts to send traffic to the web server across the VPN, the source IP address is evaluated to be contained within the local subnet of 192.168.128.0/24, which requires a translation to be performed. The MX will then map the client's IP to the equivalent IP in the translated subnet. When the example client's traffic egresses the site-to-site VPN, it will have an IP address of 10.15.30.44.
If VPN subnet translation is configured, the translated subnet will automatically be advertised to all remote site-to-site VPN participants. In this example, in order for the web server at 172.16.30.8 to communicate with the example client, traffic must be sent to 10.15.30.44 (the equivalent IP offset within the translated subnet). When the web server's traffic is sent to 10.15.30.44 and received by it's local MX, it will be routed to the appropriate remote MX and the destination IP address will be translated back to 192.168.128.44 before it egresses the MX's LAN.
When configuring VPN subnet translation for a local subnet that exists in multiple locations, the subnet duplicated subnet must be translated at each network that is configured to allow VPN access.
1-to-many (1:M) VPN NAT
Cisco Systems Vpn Client
1:M NAT for VPN allows for a subnet that is allowed in the site-to-site VPN to be translated to a single IP address. This option is ideal for large deployments where IP addresses within the site-to-site VPN must be conserved.
The functionality discussed in this part of the article is only available in beta.
Configuration
To configure 1:M NAT for VPN:
- Navigate to Security & SD-WAN >Configure > Site-to-site VPN.
- Set VPN subnet translation to Enabled. This will cause a new VPN subnet column to appear for the local networks.
- For the local subnet that must be translated, set VPN participation to VPN on with translation.
- In the VPN subnet column enter a single IP address in CIDR notation (/32) for the Local subnet.
- Click Save changes.
Operation
Please consider the following example:
- The 192.168.128.0/24 subnet is allowed in the site-to-site VPN
- To conserve IP space across the site-to-site VPN, 192.168.128.0/24 has been configured to be translated to 10.15.30.18
- A host on the corporate VLAN with an IP address of 192.168.128.44 is communicating with a web server across the site-to-site VPN with an address of 172.16.30.8
- The web server is also connected locally to another MX security appliance. This MX is a part of the site-to-site VPN.
When 1:M NAT for site-to-site VPN is configured, the MX will check the source IP address against a address translation table. When 192.168.128.44 attempts to send traffic to the web server across the VPN, the source IP address is evaluated to be contained within the local subnet of 192.168.128.0/24, which requires a translation to be performed. The MX will then map the source IP address to the IP address specified in the VPN subnet. When the example client's traffic egresses the site-to-site VPN, it will have an IP address of 10.15.30.18.
If 1:M NAT for VPN is configured, the translated subnet (10.15.30.18 in this example) will automatically be advertised to all remote site-to-site VPN participants. In this example, response traffic from the web server must be sent to the client using a destination IP address of 10.15.30.18. When the web server's traffic is sent to 10.15.30.18 and received by it's local MX, it will be routed to the appropriate remote MX.
If the web server's traffic is in response to a previously established VPN flow originating from the client, then it will be allowed through the VPN, the destination IP address will be translated back to the original client's, and the traffic will be forwarded to the original client. If the traffic is not in response to an existing flow that was originated by the client, the traffic will be dropped. Effectively, when 1:M NAT for VPN is used, the NAT is stateful and unsolicited inbound traffic will not be allowed, even if the site-to-site VPN firewall rules would permit it.
Considerations with non-Meraki VPN peers
This feature is only supported for Auto VPN and is not intended to work with non-Meraki VPN peers.
Additional Resources
