Python 3.7 break poi nt Start debugger inside a Python script PYTHO NBR EAK ‐ POI NT=0 Env Var: Set to skip all breakp oints PYTHO NBR EAK ‐ POI NT= ipd b.s ‐ et trace Env Var: breakp oint which debugger to use Getting Started import pdb;pd ‐ b.s et tra ce Start pdb inside a python script python -m pdb.
- Python Pdb Cheat Sheet
- Python Pdb Commands
- Pdb Python Cheat Sheet Printable
- Cheat Sheets For Python
- Python Pdb Example
Command line options
Configuration properties
They can be used in evaluations:? ${asm.tabs}
The Python debugger provides a debugging environment for Python programs. It supports setting conditional breakpoints, stepping through the source code one line at a time, stack inspection, and more. Working Interactively with the Python Debugger. The Python debugger comes as part of the standard Python distribution as a module called pdb. Pdb Command Reference These pdb commands and their syntax and descriptions are from the Python 3.6 documentation. Command Syntax / Description a a(rgs) Print the argument list of the current function. Alias alias name command parameter parameter. Create an alias called 'name' that executes 'command'. The command must.not. be enclosed. A cheatsheet for the Python Debugger (pdb) Stars. Most Recent Commit. Related Projects. Python (51,962)tex (1,089)latex. Pdb Commands Physics 91SI, Spring 2013 Rex Garland and Gabe Ehrlich Startup and Help python -m pdb.pyargs begin the debugger help command view a list of commands, or view help for a specific command within a python file: import pdb. Pdb.settrace begin the debugger at this line when the file is run.
You will want to set your favourite options in ~/.radare2rc since every line there will be interpreted at the beginning of each session. Mine for reference:
There is an easier interface accessible from the Visual mode, just typing Ve
Basic Commands
Command syntax: [.][times][cmd][~grep][@[@iter]addr!size][|>pipe]; Command chaining: x 3;s+3;pi 3;s+3;pxo 4;| Pipe with shell commands: pd | less! Run shell commands: !cat /etc/passwd!! Escapes to shell, run command and pass output to radare buffer Note: The double exclamation mark tells radare to skip the plugin list to find an IO plugin handling this command to launch it directly to the shell. A single one will walk through the io plugin list.` Radare commands: wx `!ragg2 -i exec`~ grep~! grep -v~[n] grep by columns afl~[0]~:n grep by rows afl~:0
.cmdInterprets command output
..repeats last commands (same as enter n)(Used to define and run macros$Used to define alias$$: Resolves to current address- Offsets (
@) are absolute, we can use $$ for relative ones@ $$+4 ?Evaluate expression
?$?Help for variables used in expressions$$: Here$s: File size$b: Block size$l: Opcode length$j: When$$is at ajmp,$jis the address where we are going to jump to$f: Same forjmpfail address$m: Opcode memory reference (e.g. mov eax,[0x10] => 0x10)???Help for?command?iTakes input from stdin. Eg?i username??Result from previous operations?s from to [step]: Generates sequence fromto every ?p: Get physical address for given virtual address?P: Get virtual address for given physical one?vShow hex value of math expr
?l str: Returns the length of string@@: Used for iterations
Positioning
Block size
The block size is the default view size for radare. All commands will work with this constraint, but you can always temporally change the block size just giving a numeric argument to the print commands for example (px 20)
JSON Output
Most of commands such as (i)nfo and (p)rint commands accept a j to print their output in json
Analyze
Function analysis (normal mode)
Function analysis (visual mode)
Opcode analysis:
Information
Mitigations:
Get function address in GOT table:pd 1 @ sym.imp<funct>Returns a jmp [addr] where addr is the address of function in the GOT. Similar to objdump -R | grep <func>
Write
Flags
Flags are labels for offsets. They can be grouped in namespaces as sym for symbols ...
yank & paste
Visual Mode:
V enters visual mode
ROP
Search depth can be configure with following properties:
Searching
Example: Searching function preludes:
Its possible to run a command for each hit. Use the cmd.hit property:
Magic files
Search for magic numbers
Search can be controlled with following properties:
Yara
Yara can also be used for detecting file signatures to determine compiler types, shellcodes, protections and more.
Zignatures
Zignatures are useful when dealing with stripped binaries. We can take a non-stripped binary, run zignatures on it and apply it to a different binary that was compiled statically with the same libraries.
Zignatures are applied as comments:
Compare files
Graphs
Basic block graphs
Call graphs
Convert .dot in .png
Generate graph for file:
Debugger
Start r2 in debugger mode. r2 will fork and attach
To pass arguments:
To pass stdin:
Commands
To follow child processes in forks (set-follow-fork-mode in gdb)
PEDA like details: drr;pd 10@-10;pxr 40@esp
Debug in visual mode
WebGUI (Enyo)

All suite commands include a -r flag to generate instructions for r2
rax2 - Base conversion
rahash2 - Entropy, hashes and checksums
radiff2 - File diffing
Examples:
rasm2 - Assembly/Disassembly
Python Pdb Cheat Sheet
rafind2 - Search
ragg2 - Shellcode generator, C/opcode compiler
Example:
rabin2 - Executable analysis: symbols, imports, strings ...
rarun2 - Launcher to run programs with different environments, args, stdin, permissions, fds
Examples:
Python Pdb Commands
My primary debugging tool is to add print statements to my programs. Print statements are very easy to use and they work well for any simple scripts. But that’s the catch: if you’re debugging an application and/or a test file, print statements won’t be enough or will just not work (in the case if tests files).
For those cases, I find that pdb, the debugger that is part of Python’s standard library, is the next best thing: also very simple to use but gives you more insight on what’s going on in your program.
All you have to do is to invoke pdb to enter in debug mode. It’s possible to either call the script with pdb as in:
or call pdb inside the script where you want to stop regular execution and start debugging – for python 3.6 and older:
Or for python 3.7 and up:
When in debugging mode you have access to the pbd console, where you can use pdb commands (listed below) and also inspect your script – like printing variable contents, for example (just type the variable’s name in the console).
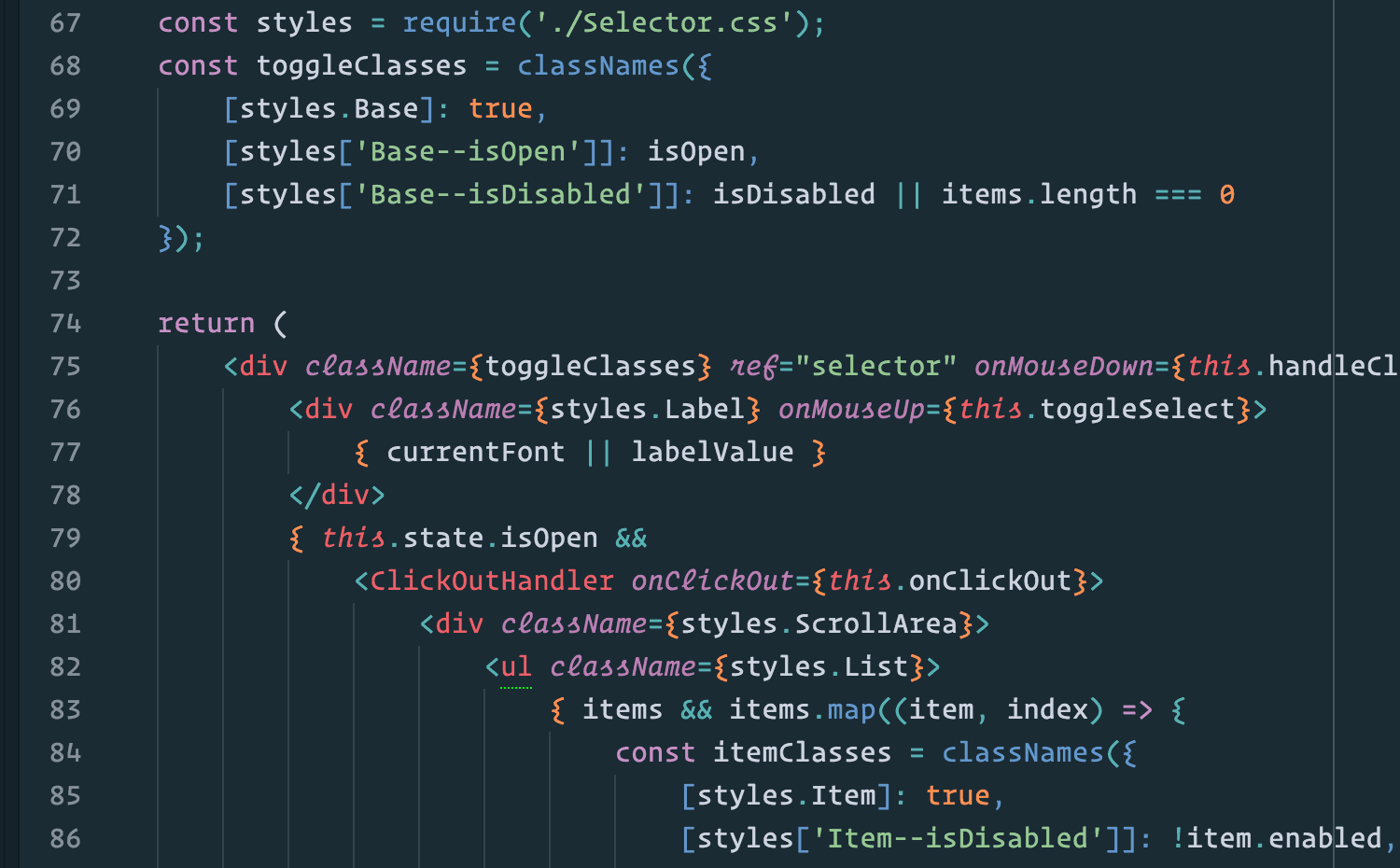
Example:
In the short script above, once the debugger console is launched, you can hit ‘n’ to reach the next line, then type ‘nb’ to read its value at that point of execution.
Personally, the most used pdb commands are the listed below but you can find the full list in the official documentation or in this free cheat sheet:
s(tep): Execute the current line, stop at the first possible occasion
Pdb Python Cheat Sheet Printable
c(ont(inue)): Continue execution, only stop when a breakpoint is encountered.
n(ext): Continue execution until the next line in the current function is reached or it returns
Cheat Sheets For Python
r(eturn): Continue execution until the current function returns.q(uit): Quit from the debugger. The program being executed is aborted.
Python Pdb Example
The postDebugging Python applications (plus free cheat sheet)was originally published atflaviabastos.ca
